Island Hospital’s mail spam filter processes roughly 15,000 – 20,000 messages a day. On average, less than 4000 of those messages are legitimate. While our mail filter has done an effective job of stemming the tide, there have been instances where cleverly crafted messages make it past our defenses. Here are a few tips and tricks to help you identify or avoid messages with malicious content:
- What does a phishing e-mail look like?
- How can I identify a phishing e-mail?
- How should I handle these?
- I clicked the link. What should I do?
- Conclusion
What does a phishing e-mail message look like?
Here is an example of what a phishing scam email message might look like:
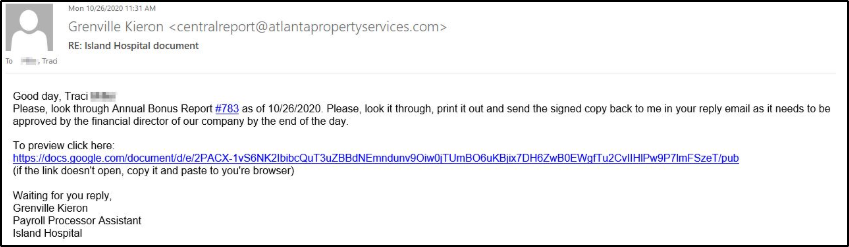
How can I identify a phishing e-mail?
Phishing e-mails often contain similar characteristics that you can keep an eye out for.
-
- Give EXTERNAL emails EXTRA attention – All messages from external senders to Island Hospital mailboxes are tagged in the subject line with the ‘[EXTERNAL]’ tag. Additionally in the body we tag the message with the ‘Stop. Think. Read’ to remind you to slow down and give this message extra scrutiny.

- Spelling and/or bad grammar – Cybercriminals are not known for their proper use of spelling and grammar. Professional organizations will have staff that edit mass mailers to ensure that messages with poor grammar or spelling do not go out to their end users. This has become less of an indicator with the advent of services such as grammarly.
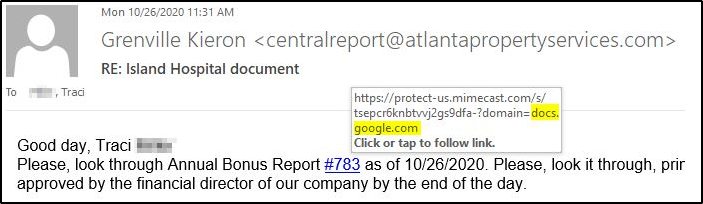
- Hover to Discover – If you see a link in a suspicious email message, don’t click on it. Hover your mouse (but don’t click) to see if the address matches the link that was typed in the message. In this example the link reveals the real web address.
- How’s it Sound? – Many time attackers will utilize e-mails that are meant to evoke emotions in an effort to get you to act on impulse versus reason. Are you being threatened with loss of access or money? Intervention from law enforcement? Is using abrasive language in the e-mail? Or does the e-mail sound to be good to be true? Promises of Something free? A great deal?
- Give EXTERNAL emails EXTRA attention – All messages from external senders to Island Hospital mailboxes are tagged in the subject line with the ‘[EXTERNAL]’ tag. Additionally in the body we tag the message with the ‘Stop. Think. Read’ to remind you to slow down and give this message extra scrutiny.
- Spoofing Popular Companies or Websites – Scam artists utilize company graphics, letterhead, etc. in phishing campaigns so that their e-mails appear to be connected to legitimate services or websites. However when you click them they redirect you to phony scam sites or legitimate-looking pop-ups.
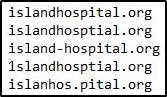
- Tricky Domains – Cybercriminals also use web addresses within their e-mails that resemble the web addresses or names of legitimate websites or well-known organization. Keep a keen eye out for any oddities within a URL or email address. In this example only one of these is correct:
How should I handle these?
- Verify the Sender – In the ‘From:’ field of your email messages always check the e-mail address that is listed. Attackers often use a familiar name, but send from an unfamiliar domain. Is the message coming from a colleague within Island Hospital? There should be a picture of your co-worker at the top of the e-mail if it is legitimate. If you recognize the name, but the message is suspicious take the time to contact the person and validate the e-mail was sent by them before taking action on it.
- Didn’t Expect It? Reject It! – If it’s not something that you were expecting and it’s unrelated to Hospital business or your job responsiblities. Toss it in the trash, worst case scenario is I.S. will have to restore that message if it was legitimate.
- Report It – Always let Information Systems know if you received a suspicious e-mail. They are able to perform additional searches to make sure no one else in the organization received the same message. Report a message from Outlook or forward your message to security@islandhospital.org
I clicked the link. What should I do?
- Don’t Panic – Contact Information Systems immediately. Our help desk staff will be able to advise you regarding next steps to remediate the issue. Early detection helps to the lower the impact malicious software can have on your workstation as well as the entire network.
- Stop Typing – Once you’ve clicked the link it’s time to stop inputting sensitive information. Chances are you’ve been redirected to a site or form that intends to capture information for malicious purposes.
Conclusion
Phishing is one of the many snares that Information Systems works to keep at bay by utilizing various technologies. However, new methods emerge on a daily basis and messages are bound to slip through. If you are the recipient of one of these types of messages, please contact Information Systems. Often times, there are measures that can be taken to help ensure those messages get properly blocked.



